What is Zero Trust Architecture (ZTA)?
The National Institute of Standards and Technology (NIST) in the U.S. define ZTA as: “an enterprise cybersecurity architecture that is based on zero trust principles and designed to prevent data breaches and limit internal lateral movement”.
ZTA pushes organizations to start with denying access to applications and data by default. Threat prevention is achieved by only granting access to networks and workloads utilizing policy informed by continuous, contextual, risk-based verification across users and their associated devices. That means that the organization should start with acknowledging that all entities are untrusted by default, least privilege access is enforced (risk-based assessment), and comprehensive security monitoring is implemented.

A ZTA must first be based on guiding principles, workflows, system design thinking, and operations. A major aspect will be the risk assessment approach.
Key guiding principles to achieve a ZTA are:
- All data sources and computing services are considered resources
- All communication is secured regardless of network location
- Access to individual enterprise resources is granted on a per-session basis
- Access to resources is determined by dynamic policy
- The enterprise monitors and measures the integrity and security posture of all owned and associated assets
- All resources authentication and authorization are dynamic and strictly enforced before access is allowed
- The enterprise collects as much information as possible about the current state of assets
For most organization, achieving a ZTA is a journey, a journey that starts with the confirmation of which guiding principle applies to them. It continues with the identification of what you have as assets, the degree of protection each asset needs (based on how critical they are to the organization), the identification of the policies and controls and their implementation. It concludes with a thorough monitoring and continual improvement.
The figure below, a reproduction of the NIST ZTA Deployment cycle, depicts key aspects for achieving a ZTA. The first past is the knowledge of our organizational context and specifically our processes, systems, and key stakeholders. Once this is well understood, a proper risk assessment can be done.
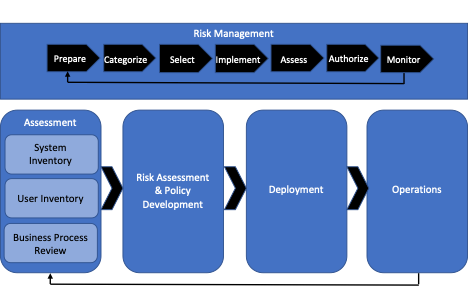
The risk assessment will be critical in defining the level of protection needed, from none to maximum level. This assessment will only be good if it is supported by a robust risk management process. When the level of protection for each asset is defined, we can proceed onto the identification of policies/controls. Finally, deployment onto operation of the approaches can start. We need to also highlight that just like any risk management process would include a feedback loop, the deployment of controls towards the achievement of ZTA also has a feedback loop, ensuring monitoring exists in operation and when applicable, continuous improvement can drive re-assessment of the organization’s context and restart the whole exercise.
The overall approach is not very complicated, but all organizations are different, and the path they will need to follow to achieve ZTA will then vary from one organization to another. Fifalde Consulting can help your organization to define your journey towards a proper Zero Trust Architecture.

